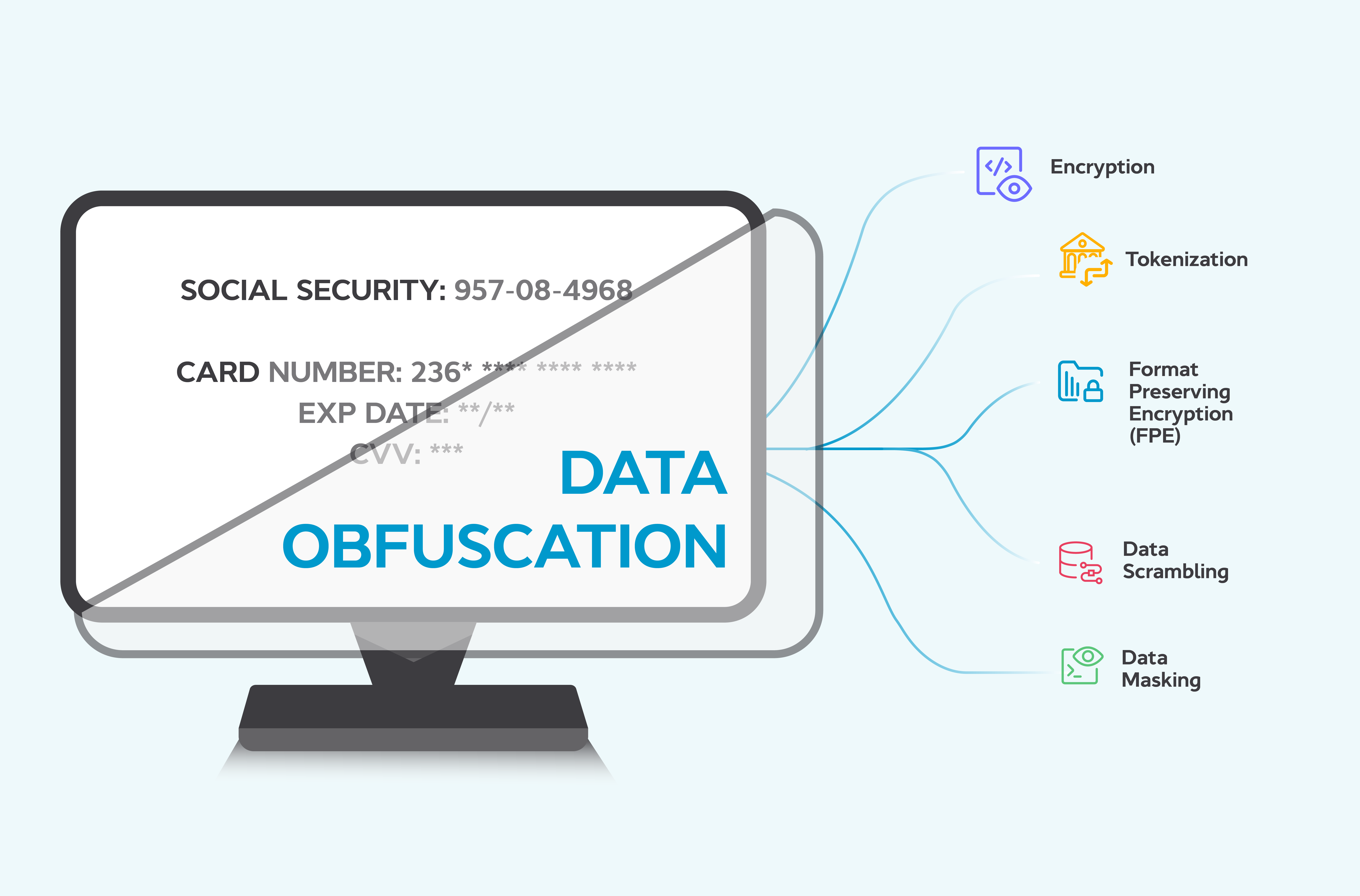
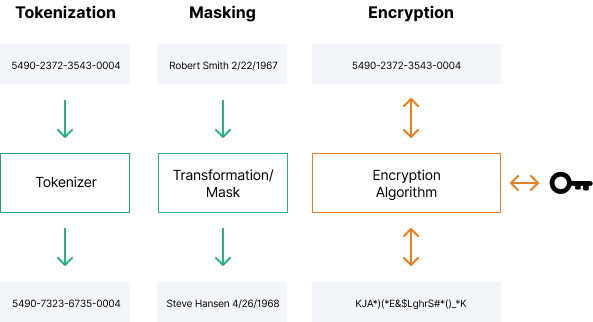
Obfuscation Techniques Ppt Powerpoint Presentation Styles Ideas Cpb | Presentation Graphics | Presentation PowerPoint Example | Slide Templates
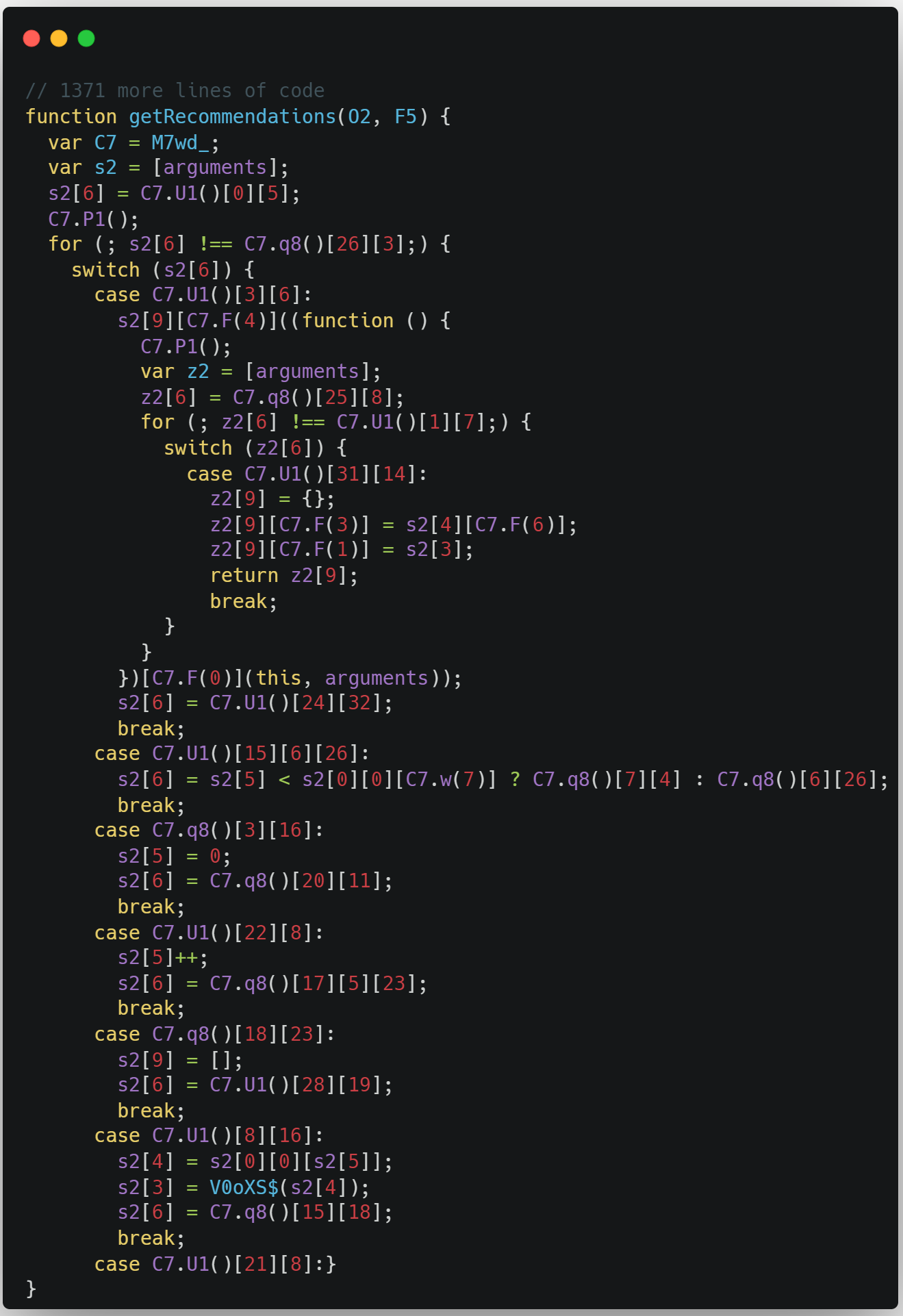
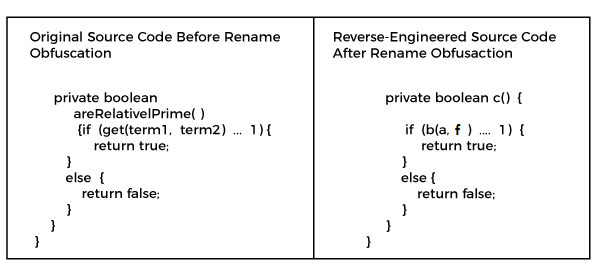
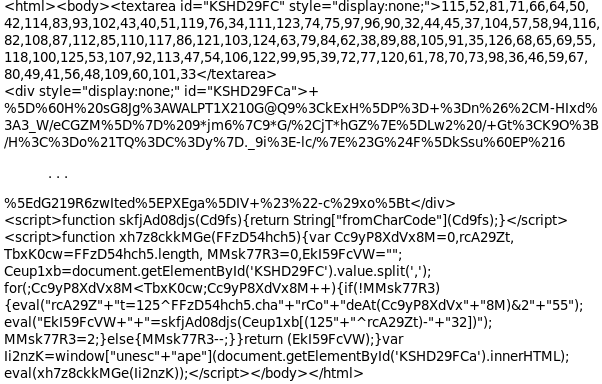
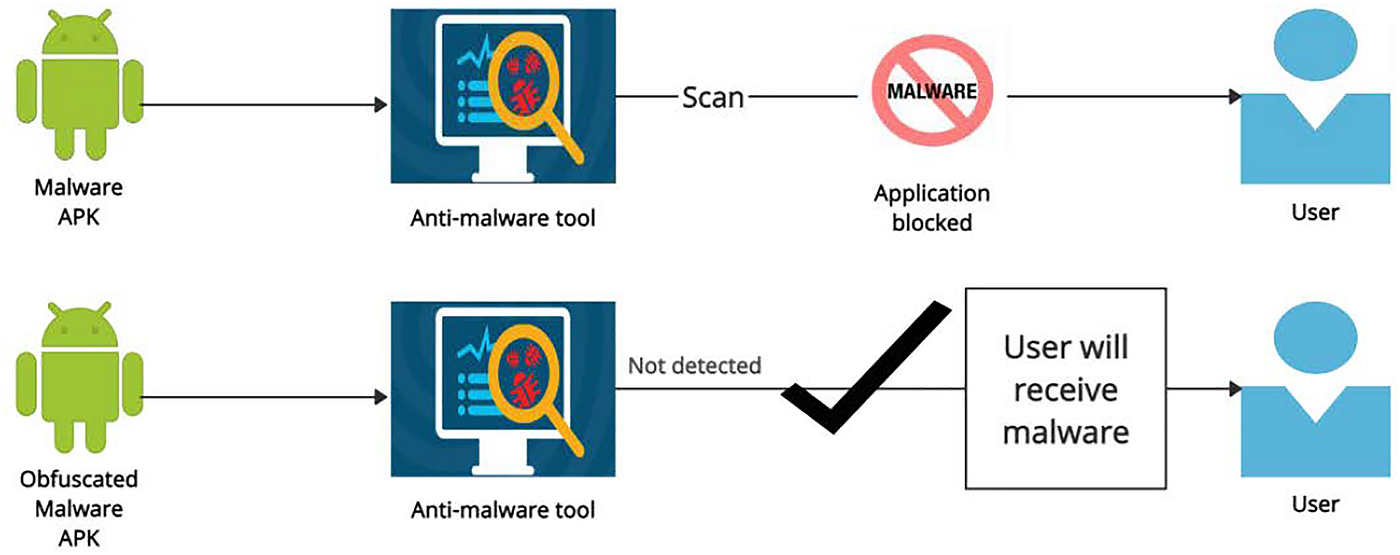
Obfuscation in Android. The process of modifying an executable… | by Supun Ishara Weerasekara | Level Up Coding
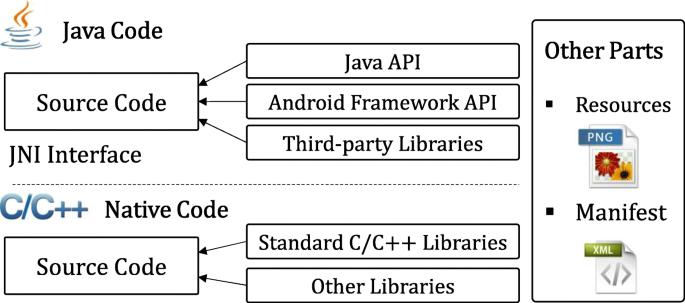
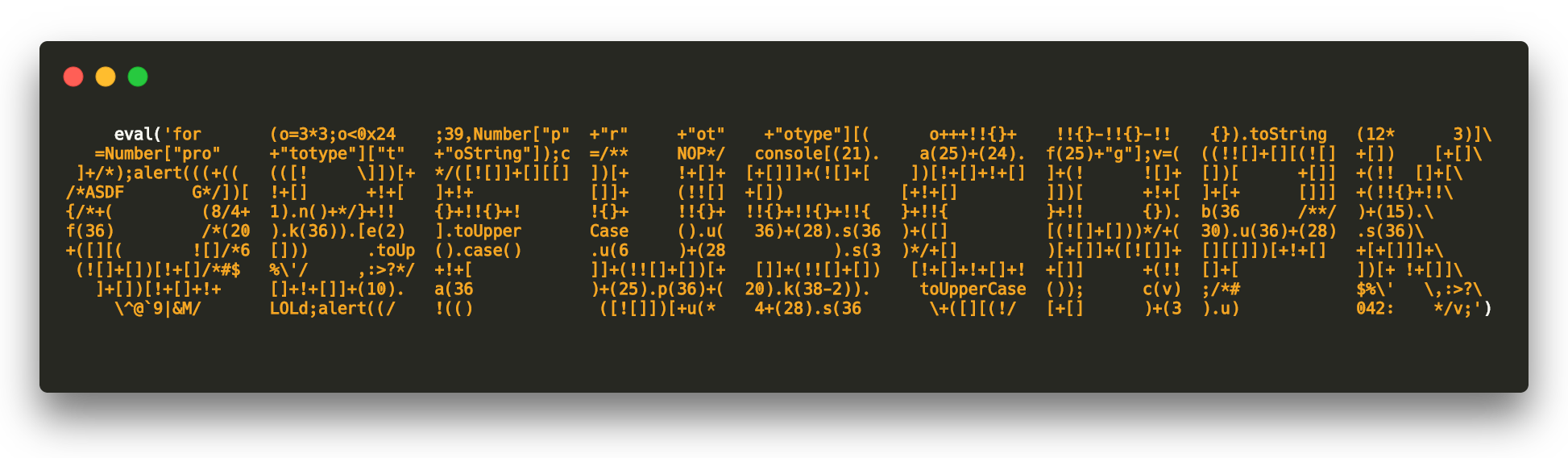
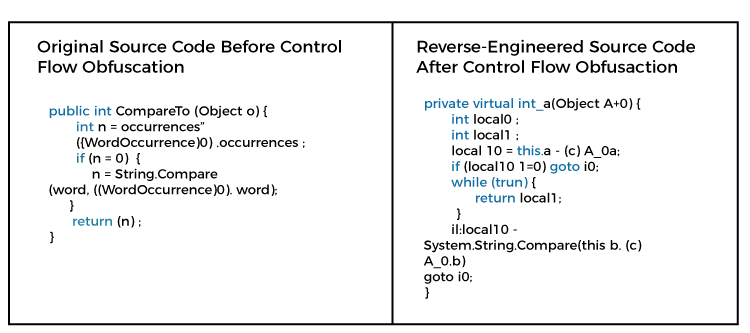
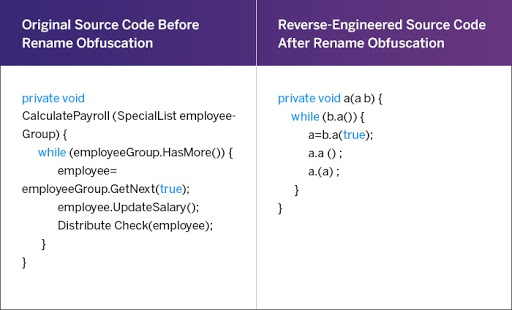
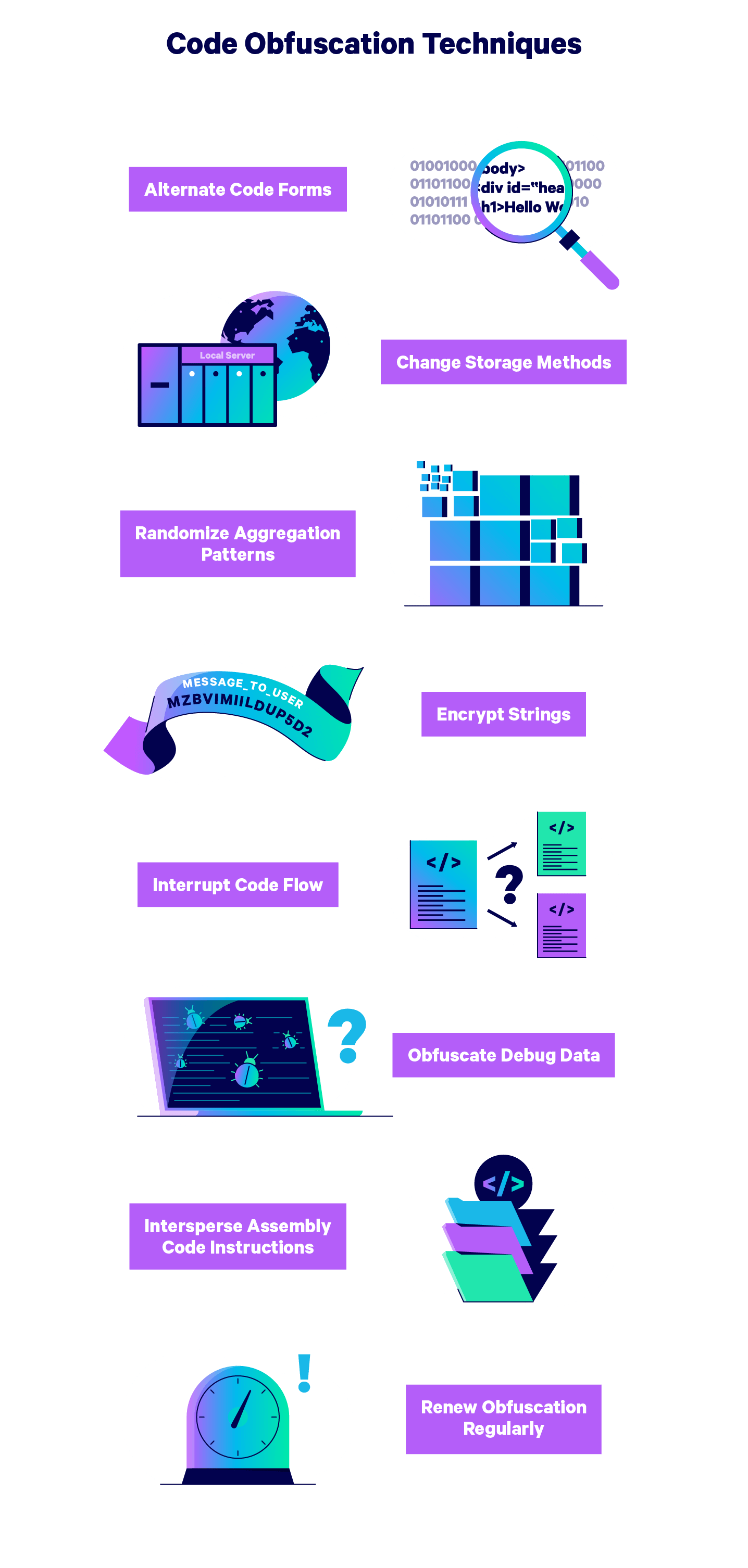
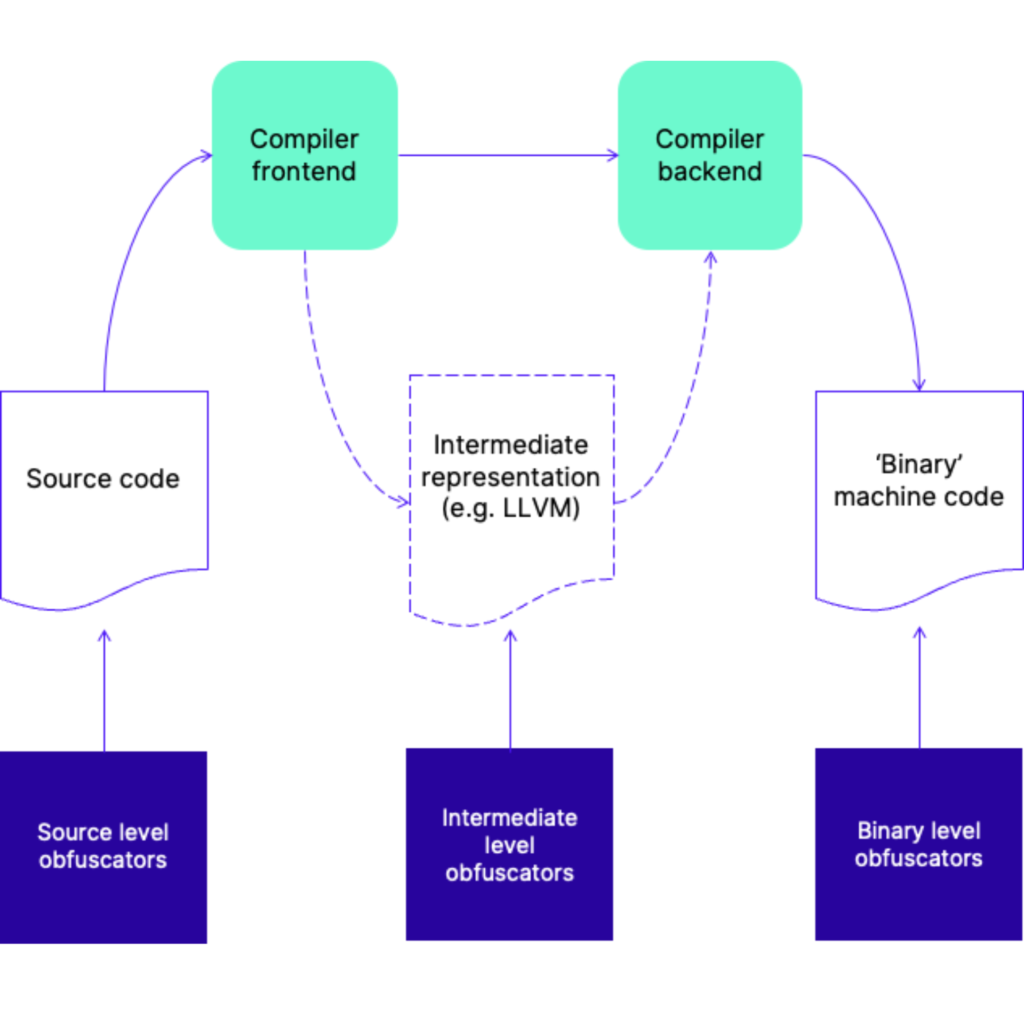
Layered obfuscation: a taxonomy of software obfuscation techniques for layered security | Cybersecurity | Full Text