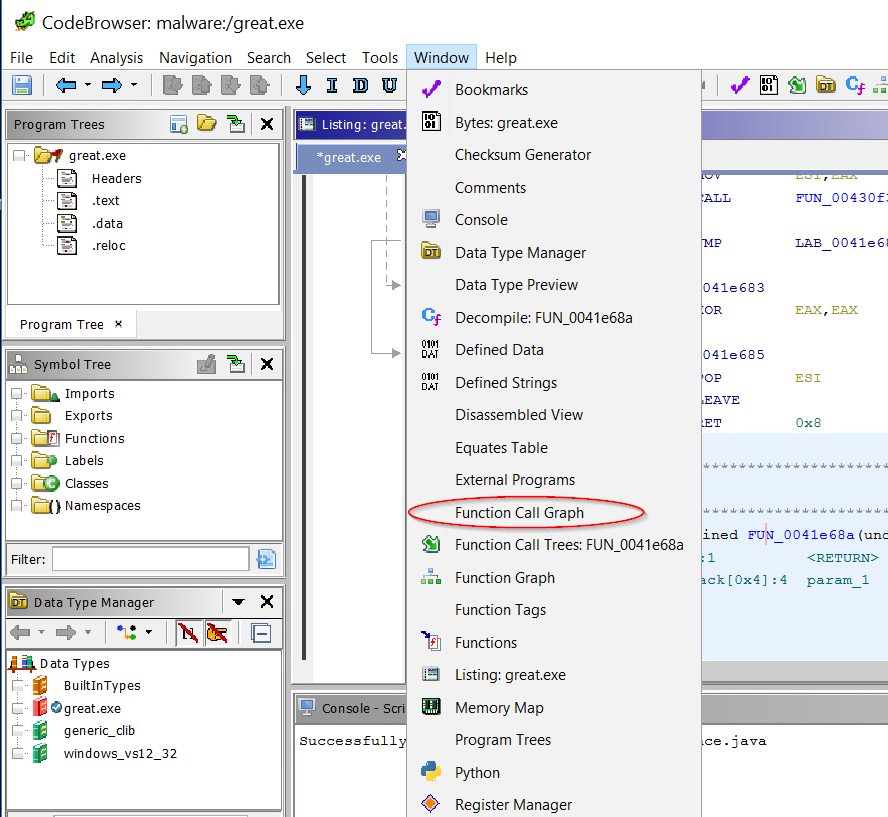
Acronis Cyber Protect Cloud, Acronis Cyber Protect 15 and Acronis Cyber Backup 12.5: Connection Verification Tool - CVT | Knowledge Base

start.me - your personal start page on X: "Explore nixintel's curated #OSINT collection! Discover tools for popular platforms like Twitter, Instagram, YouTube, as well as specialized tools for Network Investigations, Google Dorks +

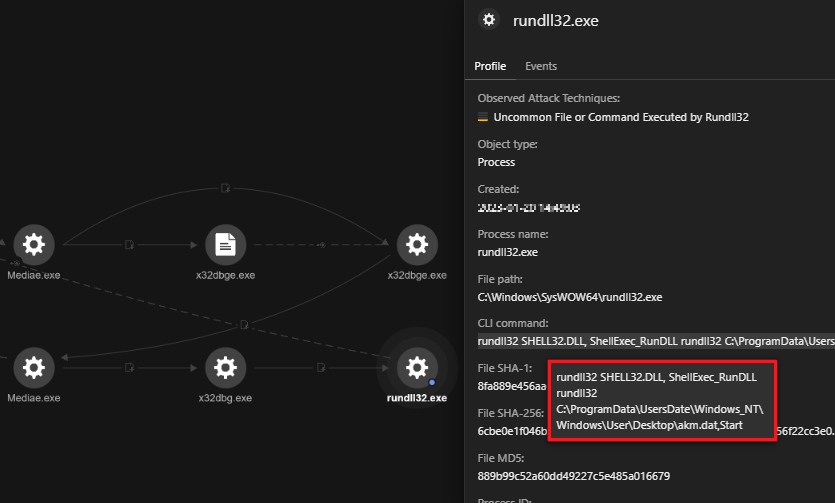
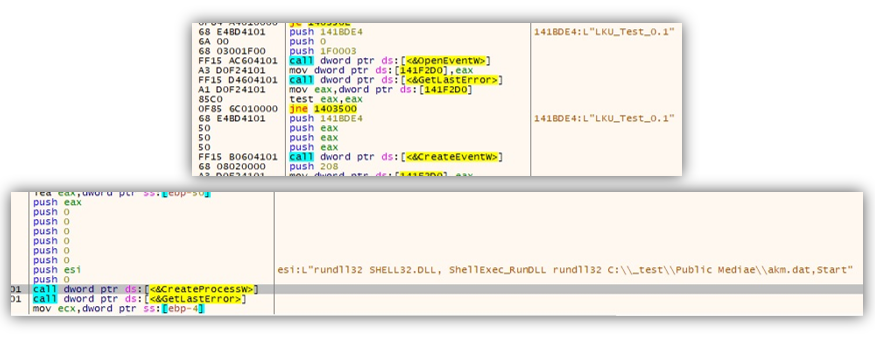
Legitimate Security Tool Emerges as Top Global Threat | Data Center Knowledge | News and analysis for the data center industry